The Failure of Traditional Security Approaches
This incident reveals several critical vulnerabilities in conventional network security strategies:
- First, while EDR solutions provide robust protection for traditional endpoints like workstations and servers, they typically don't extend to IoT devices such as webcams, printers, and other specialised hardware creating a significant blind spots in security coverage.
- Second, many organisations still rely on perimeter-based security models that assume anything inside the network can be trusted. This approach fails to account for lateral movement once attackers establish an initial foothold.
- Third, IoT devices often run on operating systems different from those used by traditional endpoints, making them compatible with alternative attack tools that may not be detected by standard security measures.
Most concerning, these devices are frequently overlooked in security monitoring strategies, allowing attackers to operate through them undetected. According to S-RM, patches were available for the webcam vulnerabilities, meaning this attack vector could have been eliminated through proper maintenance.
How Service-Based Network Segmentation Would Have Protected the Organisation
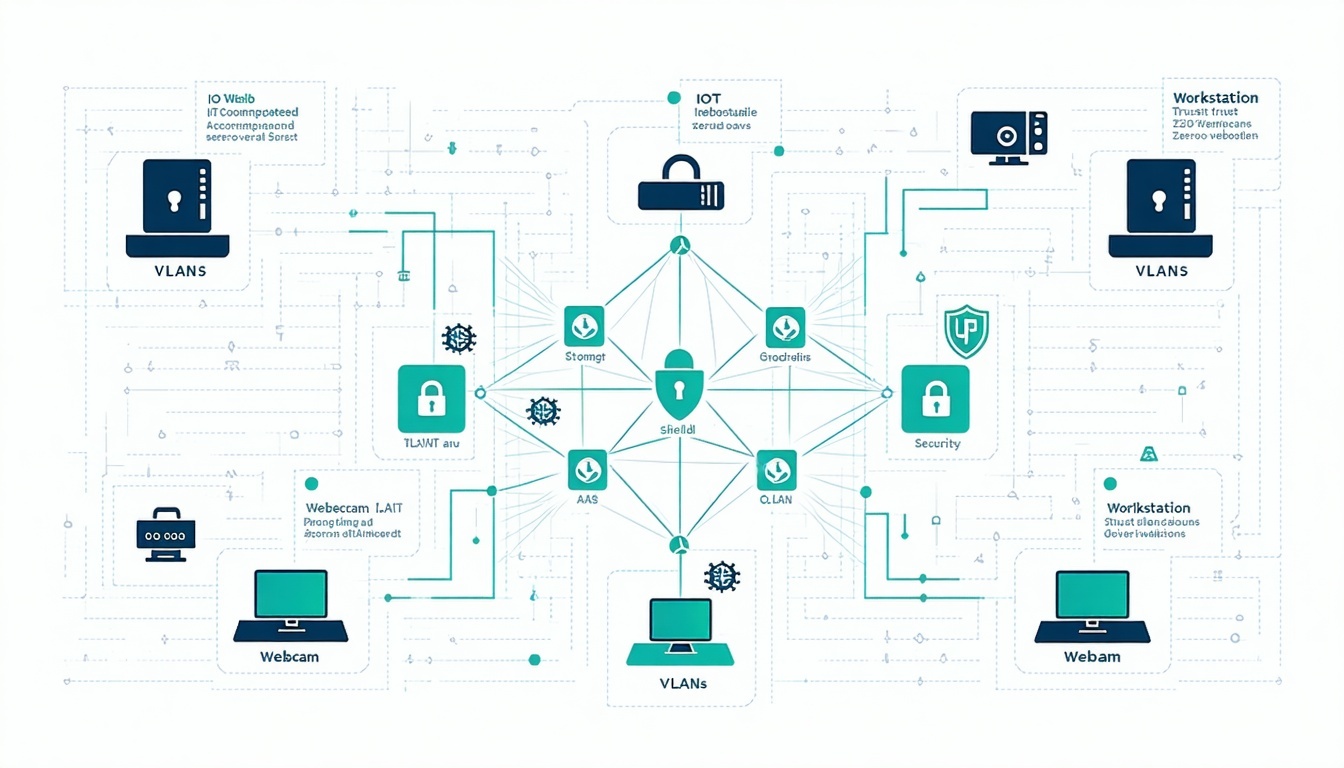
Service-based network segmentation using VLANs represents a powerful solution to the vulnerabilities exploited in the Akira attack. Network segmentation is a security approach that divides networks into isolated segments with strict access controls at each layer, significantly limiting lateral movement and containing potential breaches.
Rather than treating the network as a single trusted environment, network segmentation implements the zero trust principle of "never trust, always verify". This approach would have prevented the Akira attack in several ways:
The organisation would have placed IoT devices like webcams in isolated network segments with strict controls on what resources they could access. Even if attackers compromised the webcam, they would have been unable to mount SMB shares from these network segments.
With proper network segmentation, the threat actors would have been stopped at this point. Between the EDR and network segmentation, the encrypting of files would not have occurred and the impact would have minimised.
Implementing Effective Network Segmentation: The Microsolve Approach
Implementing effective network segmentation is never optional - no matter the size of network being deployed our team begin with thorough network planning and design based on the services being deployed. Our approach involves:
- Creating service-based VLANs that group devices by function rather than location, ensuring webcams and other IoT devices are separated from critical business assets.
- Implementing strict access controls between segments based on identity and verified need, following the zero trust principle of continuous verification.
- Deploying comprehensive monitoring solutions that track traffic between segments, ensuring even devices like webcams are included in security oversight.
- Ensuring all devices, including IoT hardware, receive regular firmware updates to patch known vulnerabilities.
Business Benefits Beyond Security
While the security advantages of network segmentation are clear, this approach offers additional business benefits:
It provides a more manageable security framework, replacing hundreds of complex firewall rules with a smaller set of identity-based policies that are easier to audit and maintain.
It supports modern work environments by enabling secure access to resources regardless of location, facilitating remote work without compromising security.
It offers improved visibility into network traffic patterns, helping organisations identify optimisation opportunities and troubleshoot performance issues more effectively.
It allows for more granular control over resource access, supporting compliance requirements for regulations like Essential8 and NIST CSF.
Conclusion
The Akira ransomware attack via an unsecured webcam represents a stark reminder that security blind spots can exist in unexpected places. As attackers become increasingly sophisticated, organisations must adopt equally sophisticated defense strategies.
Service-based network segmentation using VLANs represents a proven approach to mitigating these risks by enforcing the zero trust principle of "never trust, always verify" throughout the network. By isolating IoT devices and maintaining comprehensive monitoring, organisations can significantly reduce their vulnerability to attacks like the one perpetrated by the Akira ransomware gang.
As we continue to connect more diverse devices to our networks, the principles of zero trust and network segmentation will only become more essential to maintaining robust security postures. The time to implement these strategies is now, before attackers discover and exploit the next unexpected vulnerability in your network.